Good morning (or evening if you are on that side of the planet) folks!
We had a very busy week, packed with announcements. First, we released TheHive 4.0-RC2 which you’ve certainly taken to test, then we announced two patch releases for TheHive 3.4. And guess what? Here are some additional Cortex analyzers, a responder and a number of fixes and improvements for existing ones, bringing the total to a whopping 146 analyzers and 18 responders!
New Analyzers
- ANY.RUN sandbox analyzer, contributed by @dadokkio & @garanews from LDO-CERT (#735)
- CyberChef analyzer, contributed by @weslambert (#697)
- MalwareBazaar Hash search, contributed by @dadokkio & @garanews from LDO-CERT (#728)
- OpenCTI Analyzer, contributed by @amr-cossi (#725)
- MISPWarningList reloaded by @dadokkio & @garanews from LDO-CERT (#732)
New Responders
- RT4-CreateTicket responder, contributed by @mdavis332 (#543)
Analyzers
ANY.RUN
ANY.RUN is a malware sandbox service in the cloud. By using this analyzer, an analyst can submit a suspicious file or URL to the service for analysis and get a report. The report can contain various information such as:
- Interactive access
- Research threats by filter in public submissions
- File and URL dynamic analysis
- Mitre ATT&CK mapping
- Detailed malware reports

CyberChef
CyberChef is a simple, intuitive web app for carrying out all manner of “cyber” operations within a web browser. These operations include simple encoding like XOR or Base64, more complex encryption like AES, DES and Blowfish, creating binary and hexdumps, compression and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character encodings, and much more.
This analyzer connects to a CyberChef-server and comes in 3 flavors:
- CyberChef_FromBase64, that takes Base64 strings as input for CyberChef-server
- CyberChef_FromCharCode, that takes CharCode as input for CyberChef-server and run this recipe
- CyberChef_FromHex, that takes Hex strings as input for CyberChef-server
TheHive displays the analyzer results as follows:


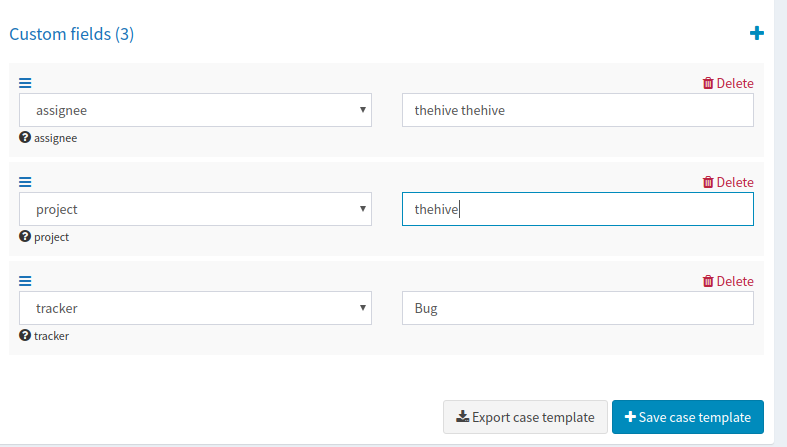
MalwareBazaar
MalwareBazaar is a project from abuse.ch with the goal of sharing malware samples with the infosec community, AV vendors and threat intelligence providers.
This analyzer allows analysts to query the API of this service on observables of types ip, domain, fqdn, url, and hash.
TheHive displays the analyzer results as follows:


OpenCTI
OpenCTI is an open source platform allowing organisations to manage their Cyber Threat Intelligence knowledge and observables. It has been created in order to structure, store, organise and visualise technical and non-technical information about cyber threats.
This analyzer allows an analyst to query the API and request for information about observables of types domain, ip, url, fqdn, uri_path, user-agent, hash, email, mail, mail_subject, registry, regexp, filename and other.
TheHive displays the analyzer results as follows:


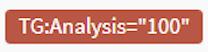
MISPWarningLists reloaded (need for speed aka DB support)
The previous version of this analyzer basically used to clone the MISP Warning lists repository and do a lookup in downloaded files. This can be very long to complete.
This new version introduces the optional support of PostgreSQL:
- To store warning lists, in a similar way to the NSRL (National Software Reference Library) Analyzer.
- Make lookups through these lists faster.
If you want to benefit from the performance boost, using a PostgreSQL server to store the data, you can simply install the requirements.txt, feed the database and configure the connection in the configuration as well:
- First, sync with the misp-warninglists GitHub repository
- In the analyzer folder, use the program warninglists_create_db.py to import the warning lists in PostgreSQL. Before running, edit the program file and update the path of where your lists are stored (
warninglists_path = "misp-warninglists/**/list.json") - You can schedule these jobs (ex. with cron): first, sync a folder with the repository, and then run the program to update the database.
Once done, configure the analyzer with the conn parameter to connect to the database, or, if you prefer to continue using the previous behaviour and do your lookups in files, just specify the path of the folder:

Templates have also been updated, and TheHive displays the analyzer results as follows:


Responders
RT4-CreateTicket
RT4 (Request Tracker) is a ticketing system. With this responder, an analyst can create a ticket in RT. CaseID is submitted to RT as a reference.
Unfortunately, like for some other analyzers and responders, we have not been able to test this responder on our side. Please feel free to share your feedback with us and also with Michael Davis, who we would like to thank for the hard work and for having shared this responder with the community.
Fixes and Improvements
- Fix Inconsistent Key References in Shodan Analyzer (#748)
- Fix SSL & python3 for Yeti Analyzer (#468 , #708)
- Fix bug in Emlparser Analyzer (#730)
- Fix in Shodan Analyzer: Inconsistent Key References (#748)
- Support python3 in DNSDB Analyzer (#613)
- Support APIKey for EmailRep Analyzer (#750)
- Improvement: EmlParser now extracts some useful IOCs (#710)
Get It While Supply Lasts!
If you are still using the old-style way of installing analyzers and responders, run the following commands:
cd path/to/Cortex-Analyzers
git pull
for I in analyzers/*/requirements.txt; do sudo -H pip3 install -U -r $I || true; done
for I in responders/*/requirements.txt; do sudo -H pip3 install -U -r $I || true; done
Once done, ensure to refresh your analyzers and responders in the Cortex WebUI. Connect as an orgadmin and go to the Organization menu. Click on the Analyzers tab and click on the Refresh analyzers button. Do the same for the Responders tab: click on the Refresh responders button. Refer to the online Cortex documentation for further details.
Update TheHive Report Templates
If you are using TheHive, you must import the new report templates in your instance as follows:
- download the updated package
- log in TheHive using an administrator account
- go to
Admin> Report templates` menu - click on
Import templatesbutton and select the downloaded package
Running Into Trouble?
Shall you encounter any difficulty, please join our user forum, contact us on Gitter, or send us an email at support@thehive-project.org. We will be more than happy to help!