Guess what? TheHive Project is still alive and well, as Saâd already mentioned in a previous blog post.
We’ve been certainly very busy lately, preparing the upcoming release of TheHive 4 and doing many other things beside working on our FOSS project. As a result, it took us a rather long time to merge several community contributions and reduce the sizeable pile of pull requests.
We would like to thank our contributors for their patience and we hope the cyberdefenders out there will enjoy the brand new Cortex-Analyzers 2.4.0 release, with many new analyzers, responders and some bug fixes & improvements, bringing the total to a whooping 138 analyzers (counting all flavors) and 10 responders!
Additionally, with this release, all analyzers are now using Python 3. No more Python 2 technodebt!

What’s New?
New Analyzers
8 new analyzers have been added to this release:
- DomainToolsIris contributed by Chuck Woodraska (#586)
- EmailRep contributed by Manabu Niseki (#467)
- IPInfo contributed by Manabu Niseki (#463)
- Maltiverse contributed by Matteo Rosi (#448)
- MalwareClustering contributed by Andrea Garavaglia (#351)
- PaloAlto Autofocus contributed by @amr-cossi (#472)
- SpamHausDBL contributed by Wes Lambert (#585)
- and TeamCymruMHR, contributed by Wes Lambert (#576)
1 analyzer has new flavors:
- PassiveTotal contributed by Brandon Dixon (#497)
New Responders
3 new responders have been added:
- KnowBe4 contributed by Kyle Parrish (#549)
- Minemeld contributed by Wes Lambert (#577)
- Wazuh contributed by Wes Lambert (#582)
Overview of the New Analyzers
DomainToolsIris
This analyzer looks up domain names, IP addresses, e-mail addresses, and SSL hashes using the popular DomainTools Iris service API.
The analyzer comes in 2 flavors:
- DomainToolsIris_Investigate: use DomainTools Iris API to investigate a
domain. - DomainToolsIris_Pivot: use DomainTools Iris API to pivot on
ssl_hash,ip, oremail.
A valid DomainTools API integration subscription is needed to run this analyzer.
TheHive displays the analyzer results as follows:


EmailRep
The EmailRep analyzer checks the reputation of an email address against the emailrep.io database.
IPInfo
This analyzer accesses IP-centric features provided by ipinfo.io. While the EmailRep API can be used without a token for limited usage, the ipinfo.io analyzer requires the configuration of an API token before use.
Maltiverse
This analyzer lets you query the free Maltiverse Threat Intelligence platform for enrichment information about a particular hash, domain, ip or url.
TheHive displays the analyzer results as follows:


MalwareClustering
Andrea Garavaglia contributed this one a long time ago and we finally merged it into the Cortex-Analyzers repository. Andrea gave a talk about the background of this analyzer at the fourth MISP summit. You can watch it here.
In order to use the analyzer, you need to point it to a Neo4j server (you need to supply the host, port, login & password).
PaloAlto Autofocus
This analyzer lets you leverage PaloAlto Autofocus services. Provided you are an Autofocus customer and you have access to their API, you need to configure the analyzer with your username and a token key.
The analyzer comes with 3 flavors:
- AUTOFOCUS_GetSampleAnalysis lets you request a full report for a given
hash. - AUTOFOCUS_SearchIOC lets you research for samples linked to specific IoCs with datatypes like
domain,fqdn,user-agent,imphash,ip,mutex,tagandurl. Please note thatmutexandtagare not default datatypes in TheHive. You need to create them in TheHive before you can leverage them. - AUTOFOCUS_SearchJSON lets you research for samples based on a complex JSON query.
Important: TheHive has no templates corresponding to this analyzer have been published yet. They will be provided in the near future.
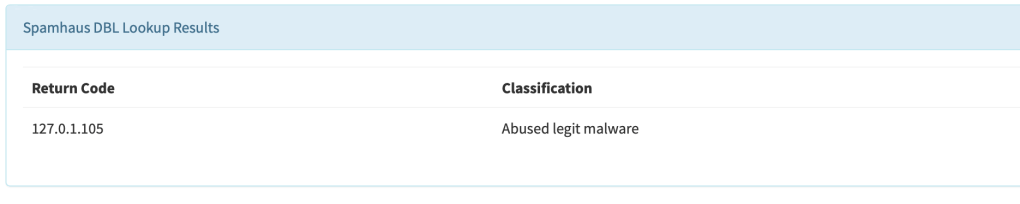
SpamhausDBL
This analyzer performs reputation lookups of a domain or a fqdn against Spamhaus Domain Block List (DBL).
TheHive displays the analyzer results as follows:

TeamCymruMHR
This analyzer queries Team Cymru’s Malware Hash Registry for known malware hashes (MD5 or SHA-1). If it is malware and known by the service, it returns the last time it has been seen along with an approximate anti-virus detection percentage.
Overview of the New Responders
KnowBe4
This responder allows the integration between TheHive/Cortex and KnowBe4’s User Events API.
If a mail observable is tagged with a specified tag, corresponding to the responder’s configuration (e.g. phished), then the associated user will have a custom event added to their profile in KnowBe4.
A valid account on KnowBe4 and an API key are required to run this responder.
Minemeld
This responder sends observables you select to a Palo Alto Minemeld instance.
To run this responder, a MineMeld Threat Intelligence Sharing account is needed.
Wazuh
This responder performs actions on Wazuh, the open source security monitoring platform. It currently supports ad-hoc firewall blocking of ip observables.
Improvements
New PassiveTotal flavors
Thanks to Brandon Dixon, the PassiveTotal analyzer gains 3 new flavors, bringing the total to 11:
- PassiveTotal_Trackers let you make tracker lookups on observables of type
domain,fqdnandip. - PassiveTotal_Host_Pairs let you make host pair lookups on observables of type
domain,fqdnandip. - PassiveTotal_Components lets you make components lookup on observables of type
domain, fqdn andip.
They come with their own report templates.
GreyNoise Analyzer
The analyzer has been updated to support GreyNoise API v2, thanks to the contribution of Whitney Champion (#562).
New Data Types Supported by Some Analyzers
- VirusTotal_GetReporthas been updated to allow requests for observables of type
fqdn. - Threatcrowd has been updated to allow requests for observables of type
domain. - Shodan has been updated to allow requests for observables of type
fqdn.
Fixes
- [#602] The MISP analyzer was bumped to version 2.1 and is ready to use PyMISP 2.4.120.
Get It While Supply Lasts!
I’m Hype
If you are using the dockerized analyzers & responders, ensure to refresh your analyzers and responders in the Cortex WebUI. Connect as an orgadmin and go to the Organization menu. Click on the Analyzers tab and click on the Refresh analyzers button. Do the same for the Responders tab: click on the Refresh responders button.
I’m Country
If you are still using the old-style way of installing analyzers and responders, run the following commands:
cd path/to/Cortex-Analyzers
git pull
for I in analyzers/*/requirements.txt; do sudo -H pip3 install -U -r $I || true; donefor I in responders/*/requirements.txt; do sudo -H pip3 install -U -r $I || true; done
Once done, ensure to refresh your analyzers and responders in the Cortex WebUI. Connect as an orgadmin and go to the Organization menu. Click on the Analyzers tab and click on the Refresh analyzers button. Do the same for the Responders tab: click on the Refresh responders button. Refer to the online Cortex documentation for further details.
Update TheHive Report Templates
If you are using TheHive, you must import the new report templates in your instance as follows:
- download the updated package
- log in TheHive using an administrator account
- go to
Admin>Report templatesmenu - click on
Import templatesbutton and select the downloaded package
Running Into Trouble?
Shall you encounter any difficulty, please join our user forum, contact us on Gitter, or send us an email at support@thehive-project.org. We will be more than happy to help!


