Thanks to the community and all the contributors, this release comes with 1 new Analyzer, 2 new Responders, lots of improvements and bug fixes.
But there is more news from the front.
Starting from this milestone, bugfixes and new Analyzers or Responders should be released in a smoother way as we are improving few processes. Some changes and recommandations should appear in the next days for submission, and our release process will be improved to fix bugs easier and release new code faster.
We also plan to offer a better documentation. We already started to publish information regarding each Analyzer and Responder. This is a work in progress, and it will be updated with the current requirements guide.
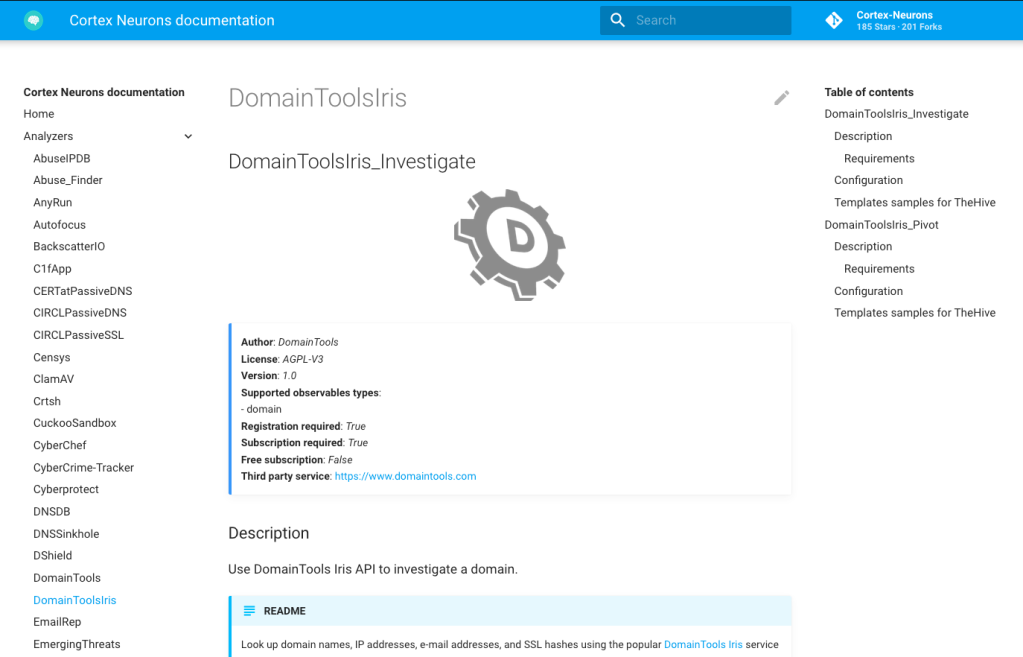
For each Analyzer and Responder, a page details the purpose of each flavors, the configuration required and even some screenshots from report samples. It will also allow developers to share their own notes if wanted.
New Analyzers
New Responders
- Sendgrid responder, contributed by @colin-stubbs (#739)
- VirusTotalDownloader, contributed by @hariomenkel (#766)
Improvements
- Refactor Onyphe using new v2 api (#736)
- Improvement in Shodan: add vulns in template and taxonomies (#772 & #776)
- Improvement in Mailer responder: tasks support and auth (#764, #737, #379)
- Improvement in SinkDb: support for new api with new dataTypes supported (#483, #498, #756)
Analyzers
LastInfoSec
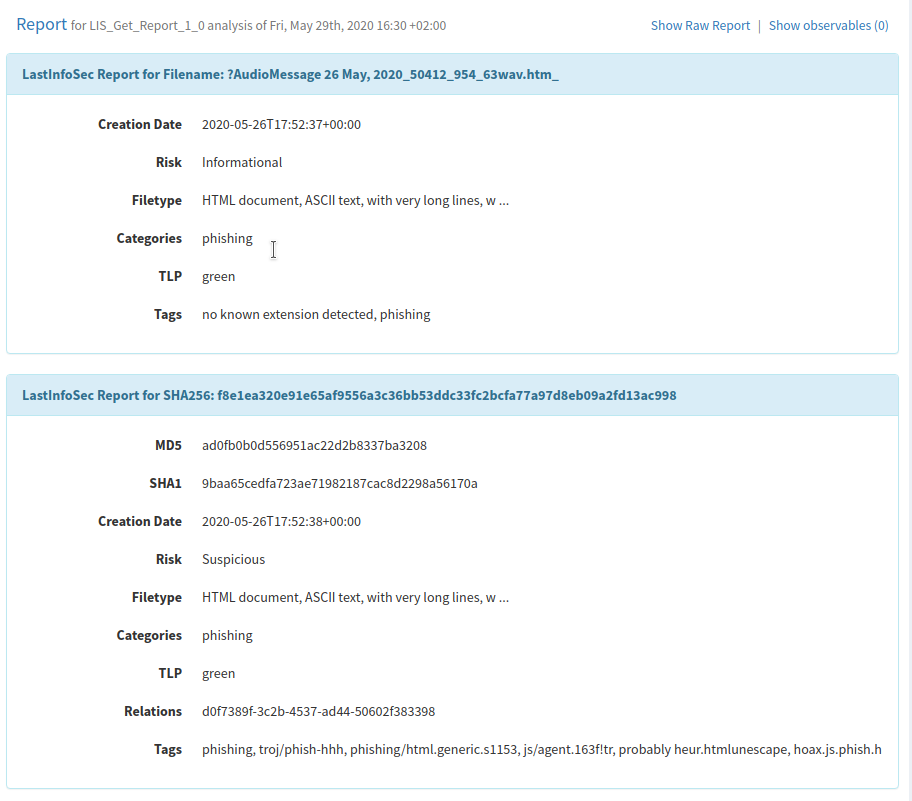
LastInfoSec offers innovative and automated solutions to collect data, refine it and turn it into useful and actionable information, quickly available to improve the protection, detection and investigation capabilities of companies and government organizations.
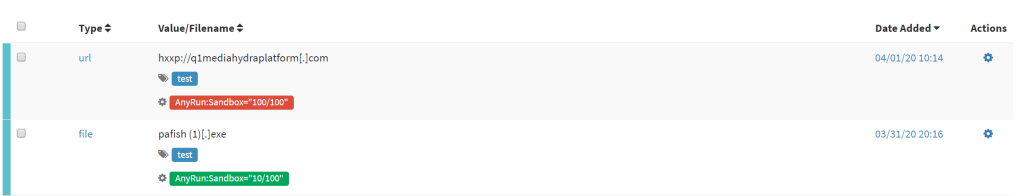
TheHive displays the analyzer results as follows:

Onyphe
An important work has been made on Onyphe Analyzer to support APIv2. All 7 flavors from older version have been removed and merged into only one flavor named “Onyphe_Summary”. An API key is still needed to query Onyphe API.
TheHive displays the analyzer results as follows:


Responders
Sendgrid
Sendgrid is a customer communication platform for transactional and marketing email used when you have to ensure that your notifications and transactional emails are delivered quickly and securely.
This analyzer works like the Mailer one, but relying on SendGrid external service to delivery emails.
In order to use the service please follow the instruction being careful to the verify your email address.
VirusTotalDownloader
This responders runs on Observables of type “hash” and allows analyst to download corresponding file from VirusTotal. Once downloaded, the file is added to the current case observables in TheHive.
In order to use this responder, a Premium API key from VirusTotal is needed. An API key from TheHive is also needed to upload the file in the observables list.

Fixes and Improvements
- Fix: some analyzer uses invalid “email” dataType (#799)
- Fix in MalwareBazaar: wrong dataTypes in config (#794)
- Fix in PhishTank: the JSON object must be str, not ‘bytes’ (#786)
- Fix in VMRay: fix error in parsing and workflow (#785 & #784)
- Fix in Wazuh: ipaddress import missing (#778)
- Fix in Minemeld Responder: requests missing in requirements (#774)
- Fix in WOT: moving to new endpoint (#771)
- DomainTools Iris: update api urls (#760)
- Fix in ThreatResponse: module_type key removed from response (#759)
- Fix in Abuse_Finder: pythonwhois dependency (#742)
Get It While Supply Lasts!
If you are still using the old-style way of installing analyzers and responders, run the following commands:
cd path/to/Cortex-Analyzers
git pull
for I in analyzers/*/requirements.txt; do sudo -H pip3 install -U -r $I || true; done
for I in responders/*/requirements.txt; do sudo -H pip3 install -U -r $I || true; done
Once done, ensure to refresh your analyzers and responders in the Cortex WebUI. Connect as an orgadmin and go to the Organization menu. Click on the Analyzers tab and click on the Refresh analyzers button. Do the same for the Responders tab: click on the Refresh responders button. Refer to the online Cortex documentation for further details.
Update TheHive Report Templates
If you are using TheHive, you must import the new report templates in your instance as follows:
- download the updated package
- log in TheHive using an administrator account
- go to
Admin> Report templates` menu - click on
Import templatesbutton and select the downloaded package
Running Into Trouble?
Shall you encounter any difficulty, please join our user forum, contact us on Gitter, or send us an email at support@thehive-project.org. We will be more than happy to help!