TheHive Project French chefs are very excited to announce the immediate availability of Mellifera, TheHive 2.11.0, the greatest and latest iteration of our flagship product.
We are thrilled to share this major version with the incident response community, for free as usual. Yes, you read that sentence right. You don’t have to cough up a single € or BTC for a platform that is as good as some commercial alternatives, unless your boss is hassling you about paying big bucks to get so-called professional support. If that’s the case, try us and you might prove them wrong.
Going through all the features and fixes of this significant overhaul will take forever (well, almost) so let us highlight a few that we feel worthy of your attention and time.
The Alerting Framework
If you need one reason to upgrade from Buckfast to Mellifera or to ditch your existing, clunky incident handling platform and use ours, then that should be its brand-new and powerful alerting framework.
With Buckfast (TheHive 2.10.x) and earlier versions, you can configure multiple MISP instances. TheHive will then poll those instances at regular intervals and display new or updated events in a specific area where analysts can preview them, import them as cases using configurable templates or ignore them altogether (and if they do so by mistake, there’s no way to go back). And if you needed to raise alerts from a SIEM, email reports or other sources of noteworthy security events, you had to rely on TheHive4py API client and create a case without having a chance to preview the events in TheHive prior to the case creation.
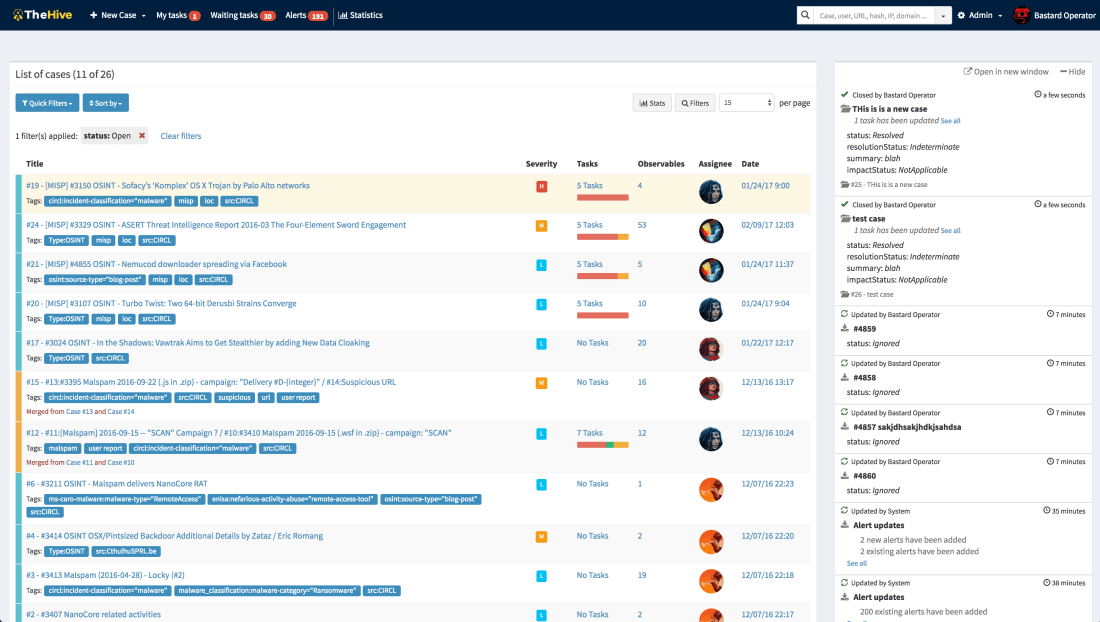
Mellifera does not have these limitations. It features an all new, fancy and efficient alerting framework which can be displayed using the Alerts button in the Web interface. This button was previously called MISP.
Within the Alerts area, you can preview not only new or updated MISP events but also any event that you have pushed through TheHive4py. The client has been modified to be compatible with Mellifera. If you have an existing TheHive4py package, please upgrade to the new 1.2.0 version using PIP.

Using TheHive4py 1.2.0, you can send your SIEM alerts, user email reports and security events from various sources to Mellifera and your analysts will be able to preview and import them or simply ignore them. If they have ignored some events by mistake, they can use the quick actions on the top of the panel to retrieve them. Please note that you have to create programs that will bridge your event sources with Mellifera through TheHive4py.

All New Skin
Mellifera has an all new skin with many refinements spread all over the interface. For example, you can now easily reorder the tasks within a case template. You can also sort task logs according to their creation date (oldest first, newest first). The flow (a.k.a live stream) is also collapsible. Moreover, when you create a case, Mellifera will suggest existing tags.
Is MISP or Cortex There?
If you have configured Mellifera to interact with at least one MISP or Cortex instance, the Web interface will show their respective logos at the bottom of the page. Please note that you can now connect to MISP and Cortex even if you are behind a proxy which requires authentication.


New Installation Packages
Starting from this release, we no longer produce all-in-one binary packages and dockers containing TheHive and Cortex. Instead you can use dockers, binaries and RPM as well as DEB packages. Wink wink.
One More Thing
Mellifera has an all new logo and the project website has been completely redesigned. Now you can see who’s behind the project thanks to Alexandre Gohier, a close friend who also happens to be a professional photographer.
Download & Try
If you have an existing TheHive installation, please follow the new migration guide.
If you are performing a fresh installation, read the installation guide corresponding to your needs and enjoy!
Support
Something does not work as expected? You have troubles installing or upgrading? No worries, please join our user forum, contact us on Gitter, or send us an email at support@thehive-project.org. We are here to help.