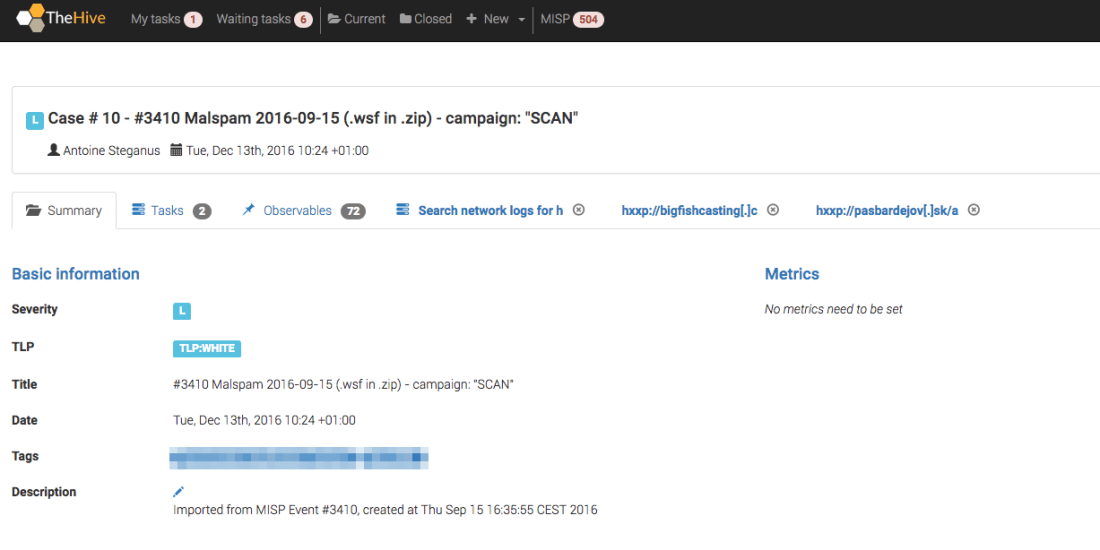
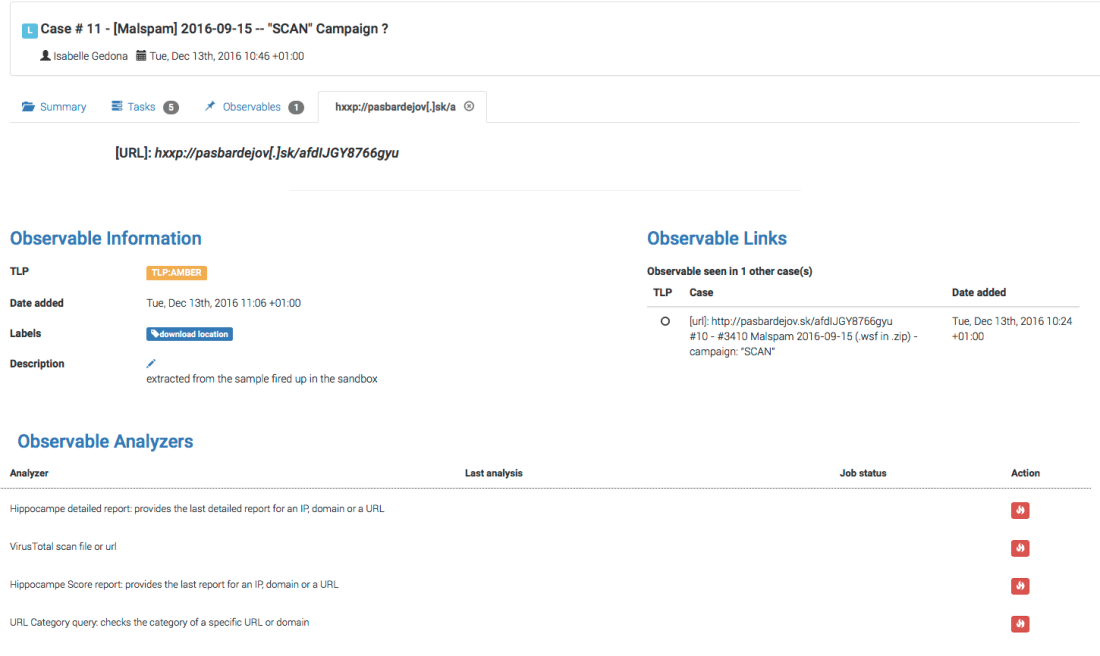
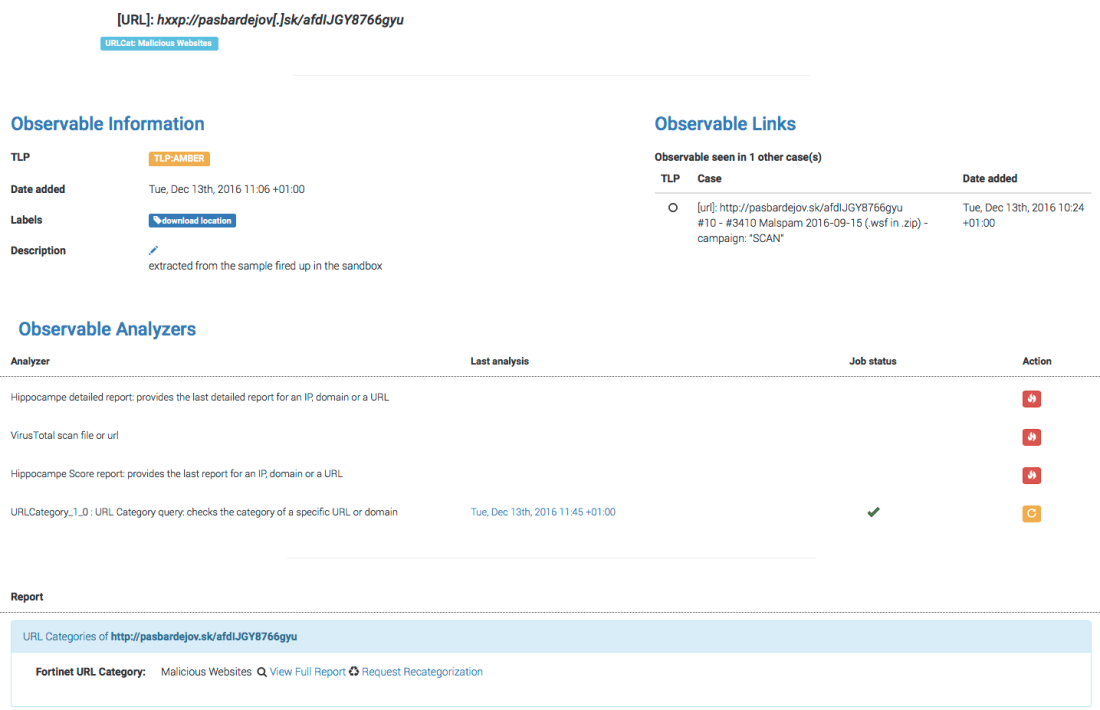
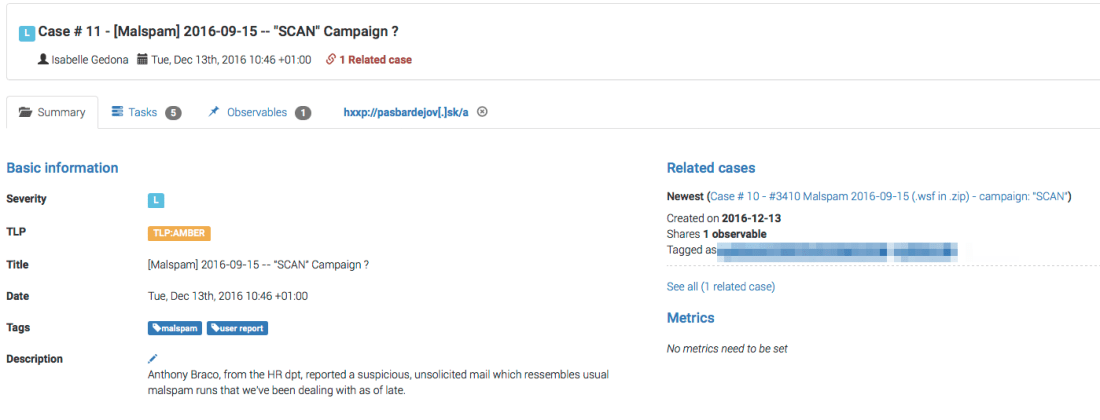
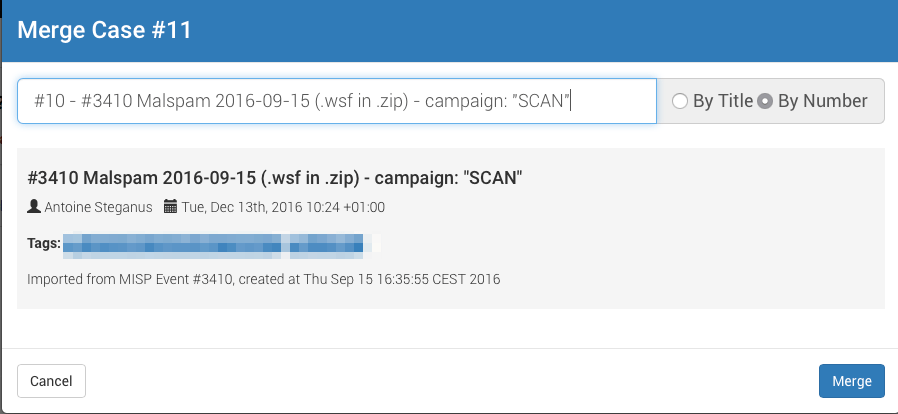
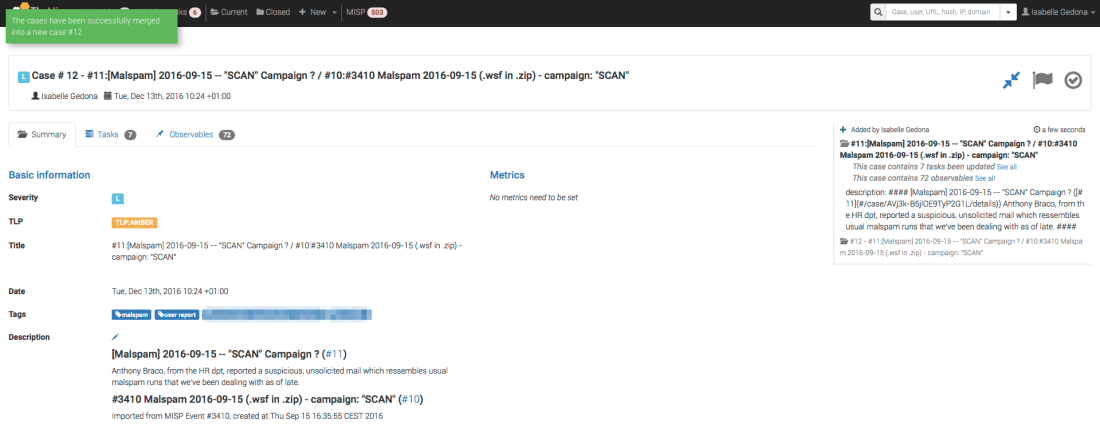
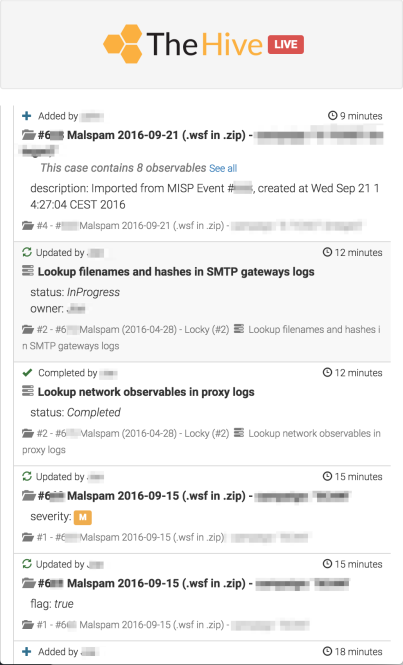
We are thrilled to announce that Cortex has two new analyzers: Joe Sandbox and MISP Search. Moreover, we have produced new analyzer report templates for TheHive and improved existing ones.
Joe Sandbox
Joe Sandbox, by Joe Security LLC, is a very powerful malware analysis platform that has been around for many years and comes in two flavors: cloud and on-premises. The Joe Sandbox Cortex analyzer has been tested using an on-prem Joe Sandbox Ultimate version and can process URLs and files. The analyzer can process files with or without Internet access.
To use the analyzer, you must provide the API key of your Joe Sandbox instance. You must log in to Joe Sandbox, click on your account name, then on Settings and on the API Key tab.
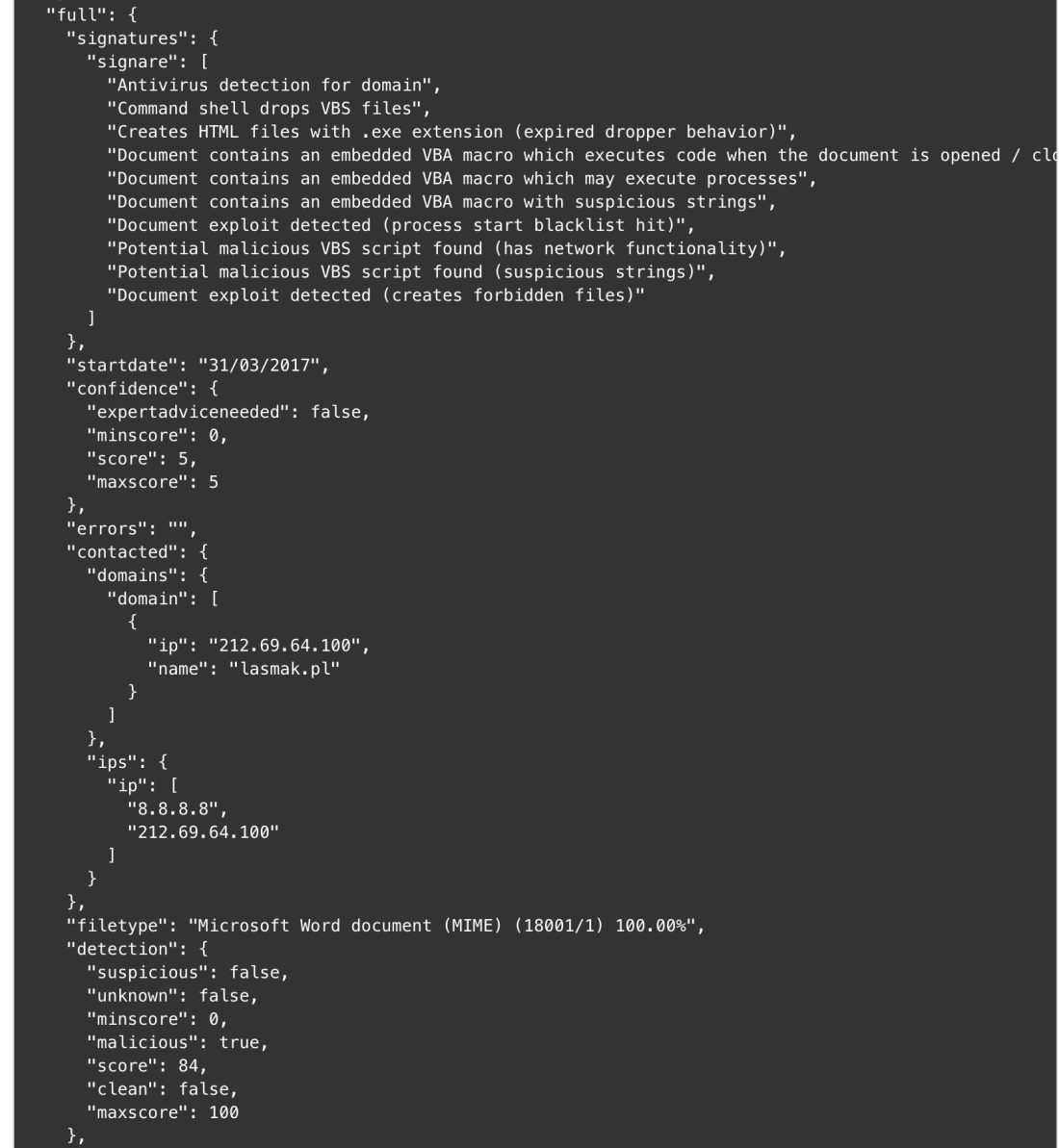
We have produced a report template for the Joe Sandbox analyzer output resulting from file analysis. The URL analysis report template is not yet available but it should be in a few days.
![]()

MISP Search

It is no longer necessary to present MISP, the de facto standard of threat sharing. The new MISP Search analyzer will let you search events containing the observable you provide as an input. It applies to a lot of observable types as you can see in the screenshot above.
To use it, you’ll need to supply the API key available in the MISP UI interface.
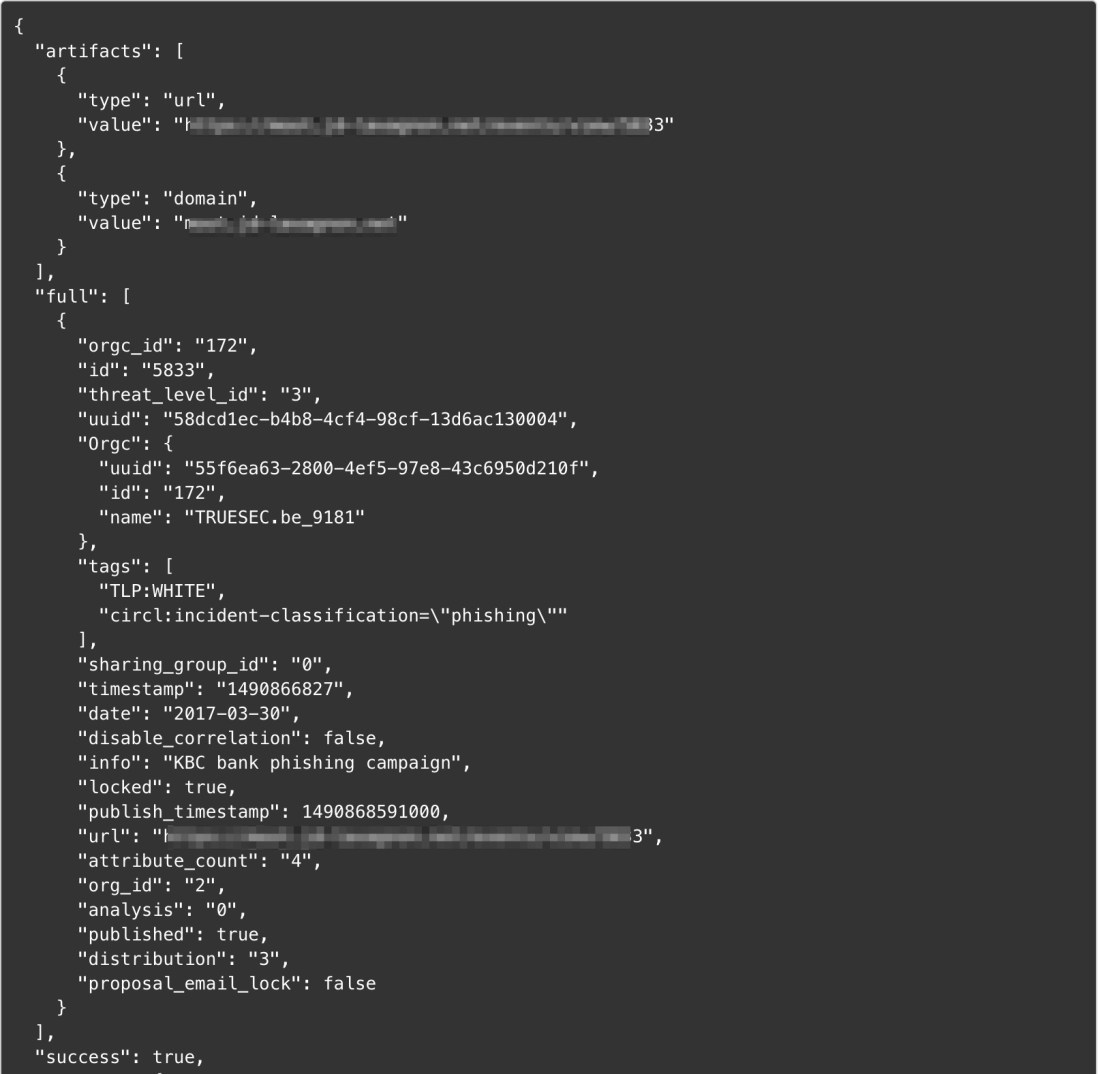
Nils Kuhnert created an alternate MISP Search analyzer which has the ability to query multiple MISP instances. We are currently reviewing his submission along with several other analyzers he contributed before improving the newly released MISP Search analyzer.
PassiveTotal Report Templates
![]()
![]()
While we published the PassiveTotal analyzer weeks ago, TheHive didn’t have report templates for it at the time. We have now new, shiny short and long report templates for most of the services provided by the PT analyzer.
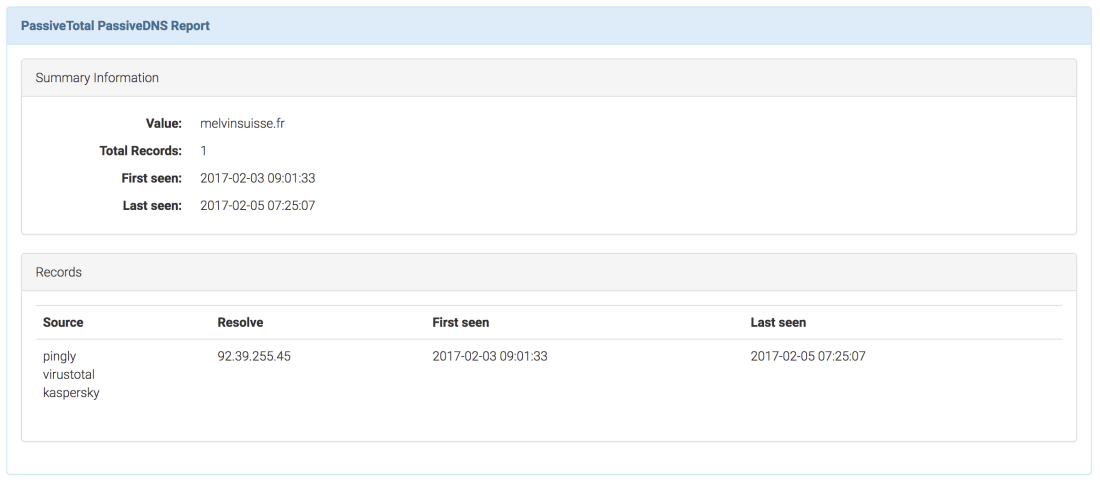
DomainTools Whois Lookup Report Template
![]()
The short report templates of the DomainTools Whois Lookup analyzer has been improved. We now use a taxonomy to provide more context and differentiate between the DomainTools and PassiveTotal Whois results.
VirusTotal Get Report and VirusTotal Scan Report Templates
![]()
![]()
The short report templates for both services have also been improved to use a taxonomy to provide additional context and distinguish their results from the PassiveTotal Malware service.
Get the new analyzers
To install the new analyzers, grab the Cortex-Analyzers repository and unpack its content (or git pull the master branch) in your existing /path/to/cortex-analyzers.
The Joe Sandbox analyzer does not need any additional Python library if you have already installed Cortex and the analyzers following the guide we provide. To use it, edit your Cortex configuration file (/path/to/cortex/application.conf) and add the following lines in the analyzer section:
JoeSandbox {
apikey="..."
url="..."
}
By default, Joe Sandbox will time out the analysis after 30*60 seconds (30 minutes). Additionally, the analyzer will wait for the Joe Sandbox server to respond within 30 seconds. If no response is received within this period, it will time out. If you want to override these values, you’ll need to add the following lines in the analyzer section:
JoeSandbox {
apikey="..."
url="..."
analysistimeout=<NEW VALUE> # optional
networktimeout=<NEW VALUE> # optional
}
The MISP Search analyzer requires pymisp. Use the following command line to install the required library:
sudo pip install pymisp
Then edit your Cortex configuration file (/path/to/cortex/application.conf) and add the following lines in the analyzer section:
MISP {
api_key="..."
url="..."
}
Please note that you must restart Cortex to take the changes into account. The current version has no persistence so you’ll lose all your existing jobs.
You can find the full installation requirements for Cortex and Cortex-Analyzers on the Cortex wiki pages.
Use the New Report Templates
To import the new report templates in your instance of TheHive:
- download the updated package
- log in TheHive using an administrator account
- go to
Admin>Report templatesmenu - click on
Import templatesbutton and select the downloaded package
Running Into Trouble?
Shall you encounter any difficulty, please join our user forum, contact us on Gitter, or send us an email at support@thehive-project.org. We will be more than happy to help you!



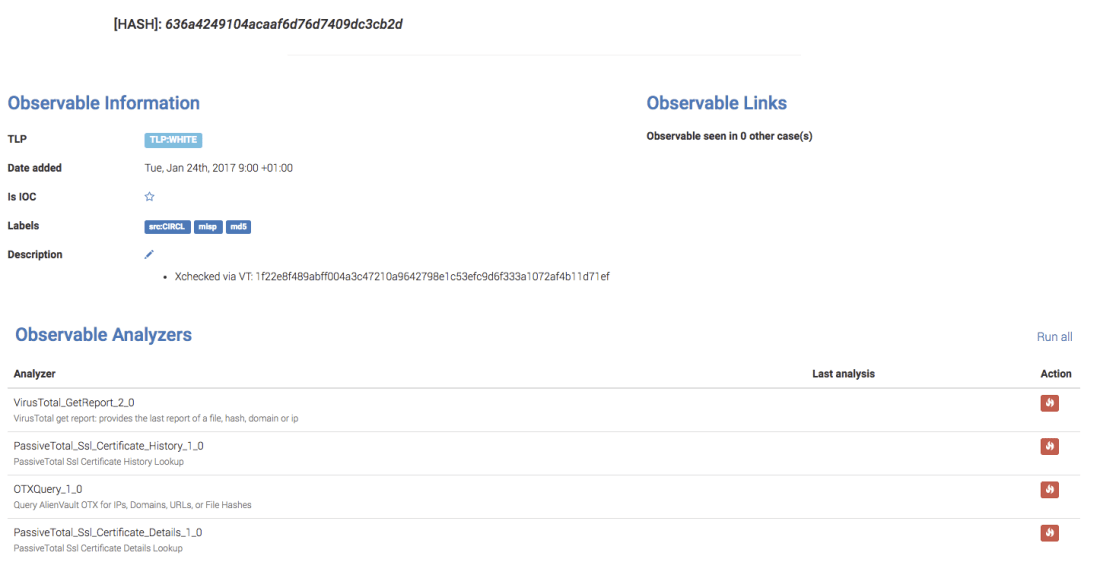 This TLP:WHITE hash was imported from a MISP event published by our good friends at
This TLP:WHITE hash was imported from a MISP event published by our good friends at 

 Short reports come in 4 colors. Red means danger (what else?). Orange means suspicious. Green means innocuous. And blue is informational. OK but what does this have to do with the title of this post?
Short reports come in 4 colors. Red means danger (what else?). Orange means suspicious. Green means innocuous. And blue is informational. OK but what does this have to do with the title of this post?