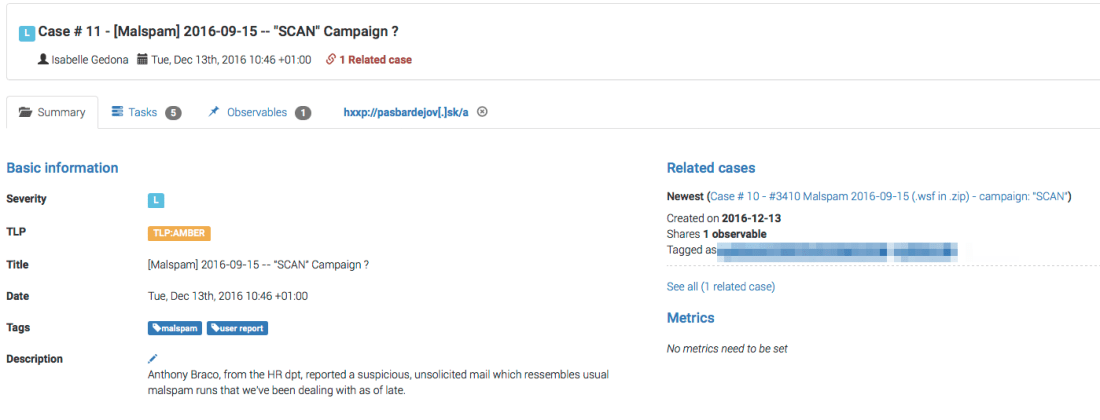
When you use TheHive, running an analyzer on an observable through Cortex will generate a long report and, in most cases, a short report as well.
Let’s see how this works in practice through an example. Assume we are trying to assess whether the 636a4249104acaaf6d76d7409dc3cb2d MD5 hash is malicious or not:

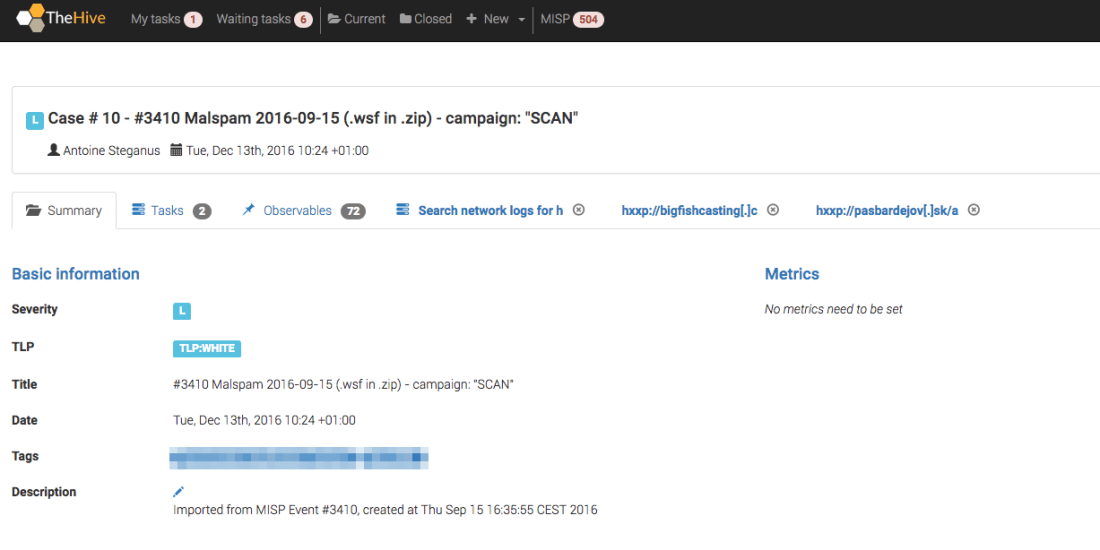
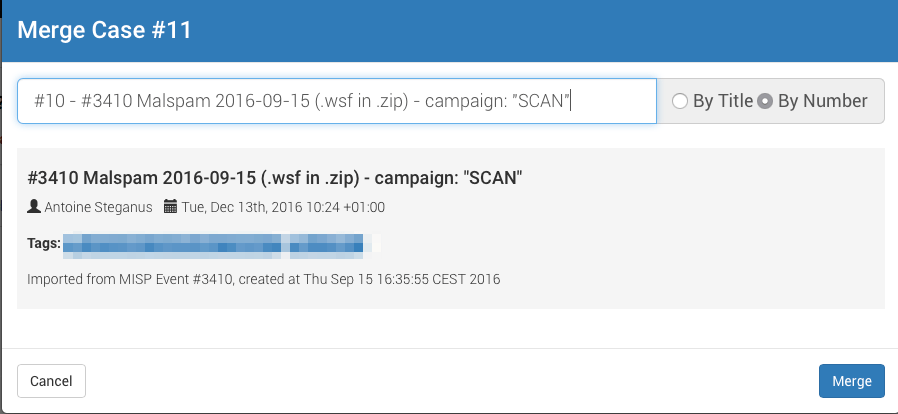
We start by clicking on it, which will open a new tab: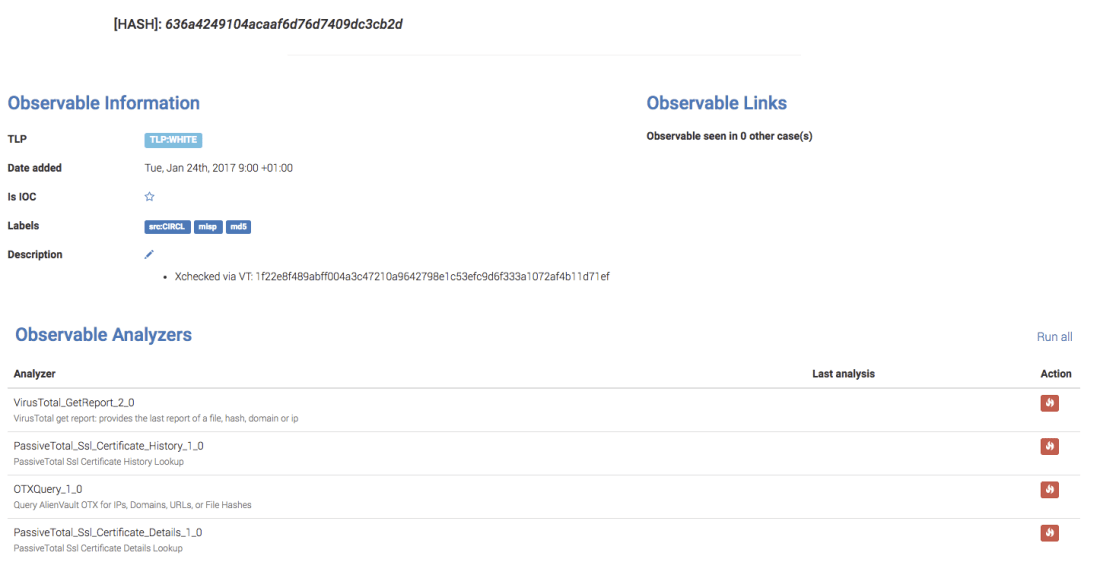 This TLP:WHITE hash was imported from a MISP event published by our good friends at CIRCL.lu sometimes ago. As you can see from the screenshot above, no analyzer was executed on it. Let’s check if it is known to VirusTotal (VT). To do so, we just need to click on the fire icon located at the right side of the VirusTotal_GetReport_2_0 row.
This TLP:WHITE hash was imported from a MISP event published by our good friends at CIRCL.lu sometimes ago. As you can see from the screenshot above, no analyzer was executed on it. Let’s check if it is known to VirusTotal (VT). To do so, we just need to click on the fire icon located at the right side of the VirusTotal_GetReport_2_0 row.

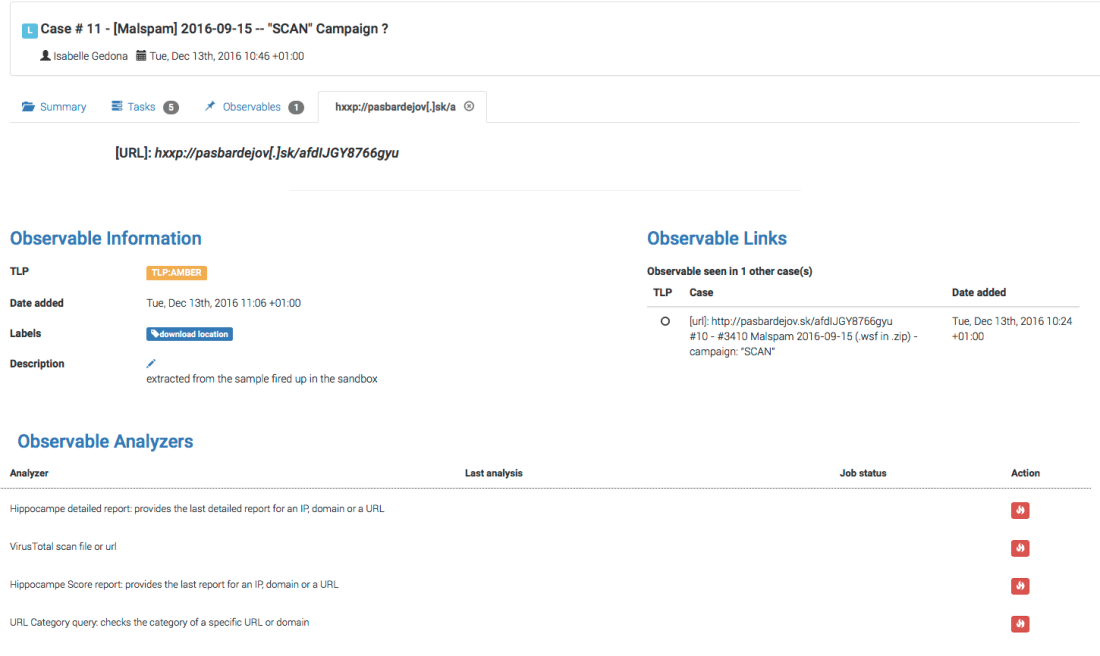
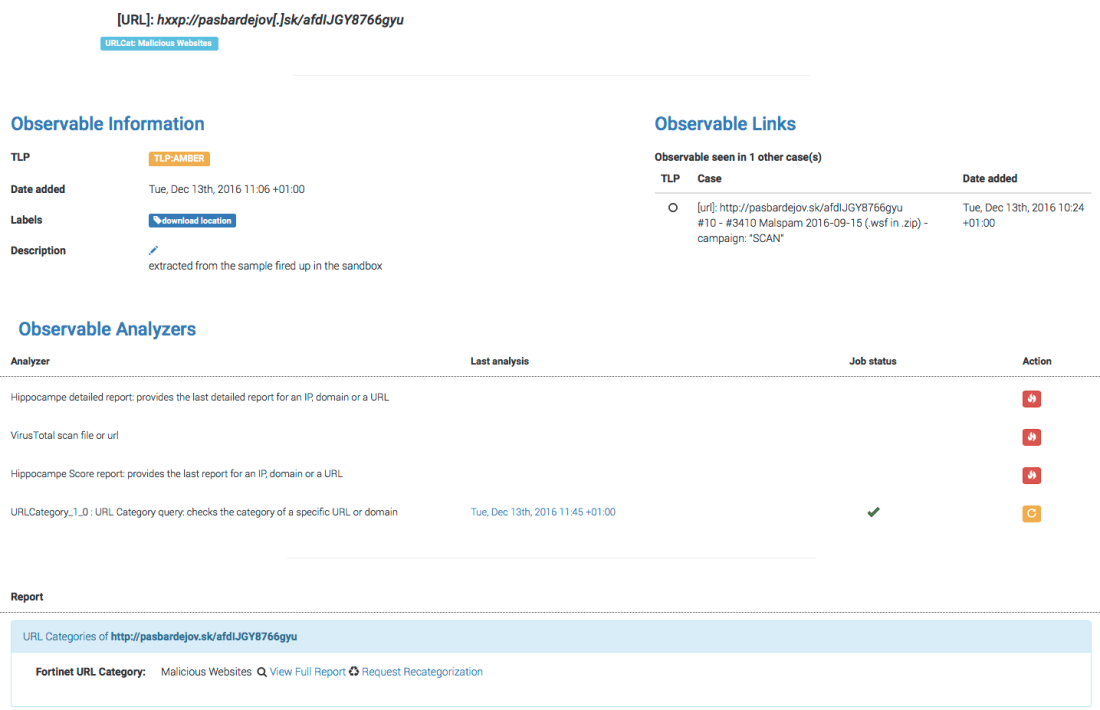
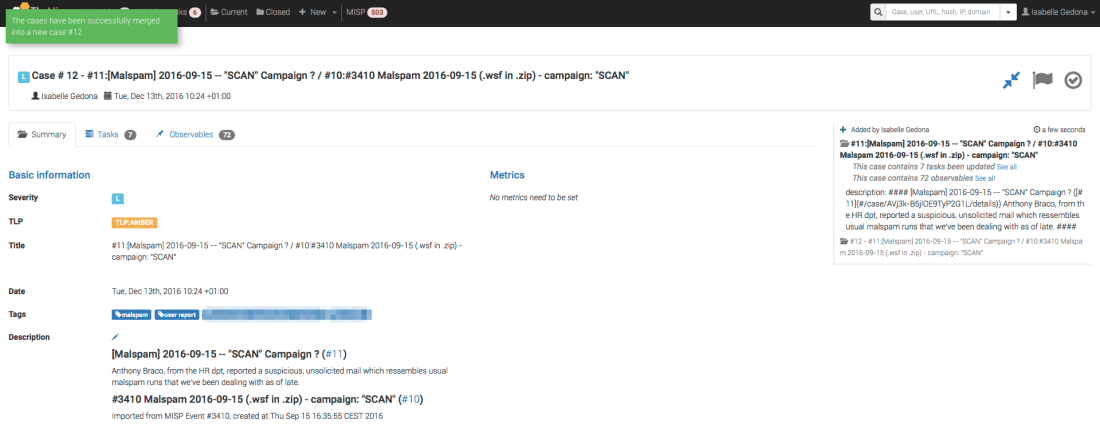
A blink of an eye later, the job has finished successfully as we can tell from the green checkmark. Clicking on the date will let us see the long report, presented according to a report template that we freely provide with most analyzers to the exception of PassiveTotal (but in a few days, PT will also get its own nifty templates).
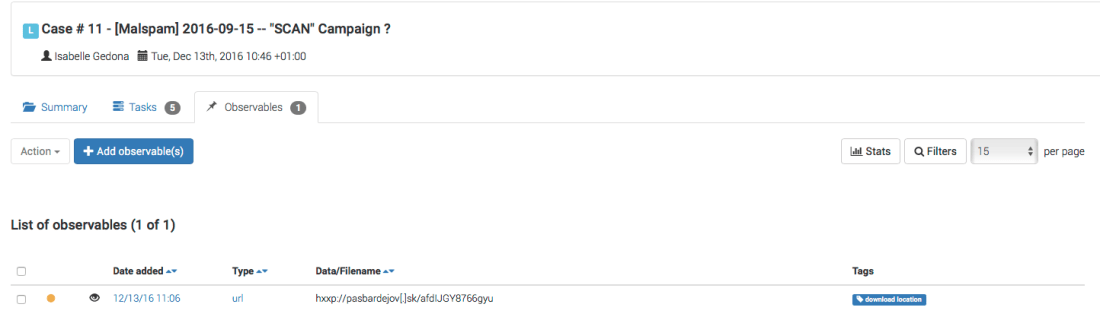
Since we are checking whether VT knows a hash or not, it will give us the results if any corresponding to the last time the associated file was scanned on the service. In our case, this dates back to Dec 2, 2016.
When the analyzer was executed, it also produced a short report which TheHive displays below the observable: Short reports come in 4 colors. Red means danger (what else?). Orange means suspicious. Green means innocuous. And blue is informational. OK but what does this have to do with the title of this post?
Short reports come in 4 colors. Red means danger (what else?). Orange means suspicious. Green means innocuous. And blue is informational. OK but what does this have to do with the title of this post?
A few days ago, while working on a new set of analyzers, Nils Kuhnert reported an issue in Buckfast 1 (2.10.1) pertaining to short reports on observables. When he ran some analyzers that should have produced short reports, he didn’t get any. When he reverted to Buckfast 0 (2.10.0), it worked. We tracked down the problem and found that our build process was the culprit. The all-in-one binary package which was supposed to contain Buckfast 1 and Cortex was in fact a 2.10.0 TheHive snapshot that had a regression. We have uploaded a fresh all-in-one binary package with Buckfast 1 instead of the development snapshot.
If you have grabbed the binary all-in-one package, please download it again and update your instance. If you are using a docker version or built Buckfast 1 from sources, you are fine. To make sure you are running the right version, click on your username once you are logged in then on About TheHive. You should see the following information:
We are going to review our release process from the ground up to ascertain such errors never occur again. We expect it to be ready for Mellifera, our next major release of TheHive. Please note that starting from that release, we will no longer provide all-in-one binary and docker packages. Instead, we’ll have separate packages for TheHive and Cortex. TheHive4py and the upcoming Cortex4py will be made available through PIP.